At the end of this page, you can find the full list of publications.
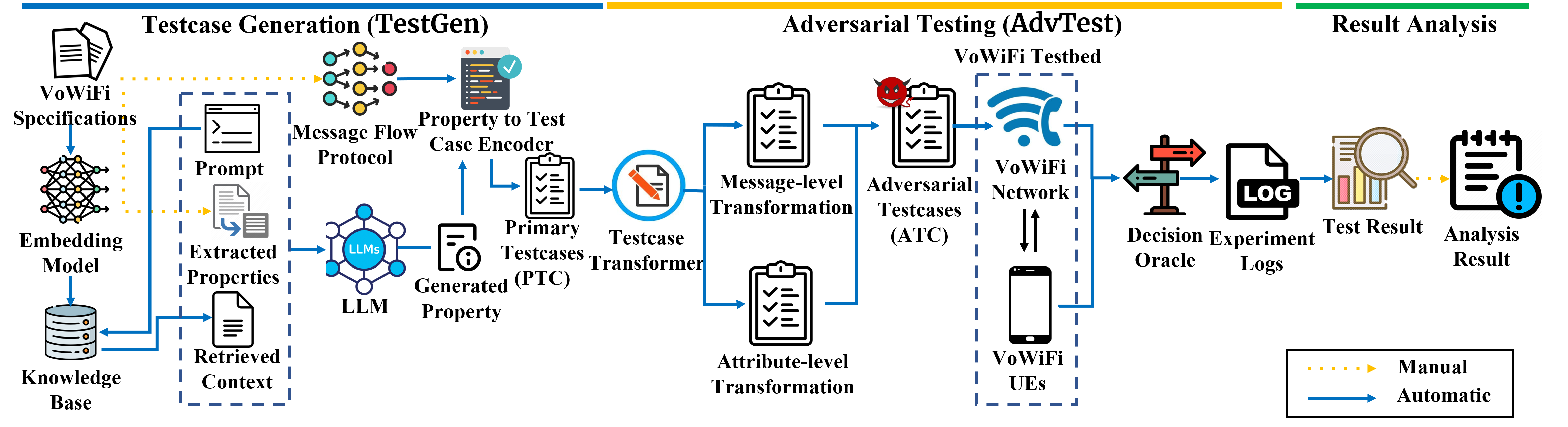
We present VWAttacker, the first systematic testing framework for analyzing the security of Voice over WiFi (VoWiFi) User Equipment (UE) implementations. VWAttacker includes a complete VoWiFi network testbed that communicates with Commercial-Off-The-Shelf (COTS) UEs based on a simple interface to test the behavior of diverse VoWiFi UE implementations; uses property-guided adversarial testing to uncover security issues in different UEs systematically. To reduce manual effort in extracting and testing properties, we introduce an LLM-based, semi-automatic, and scalable approach for property extraction and testcase (TC) generation. These TCs are systematically mutated by two domain-specific transformations. Furthermore, we introduce two deterministic oracles to detect property violations automatically. Coupled with these techniques, VWAttacker extracts 63 properties from 11 specifications, evaluates 1,116 testcases, and detects 13 issues in 21 UEs. The issues range from enforcing a DH shared secret to 0 to supporting weak algorithms. These issues result in attacks that expose the victim UE’s identity or establish weak channels, thus severely hampering the security of cellular networks. We responsibly disclose the findings to all the related vendors. At the time of writing, one of the vulnerabilities has been acknowledged by MediaTek with high severity.
Imtiaz Karim*, Hyunwoo Lee*, Hassan Asghar, Kazi Samin Mubasshirm, Seulgi Han, Mashroor Hasan Bhuiyana, and Elisa Bertino, (* joint first authors)
IEEE International Conference on Computer Communications (INFOCOM), 2026
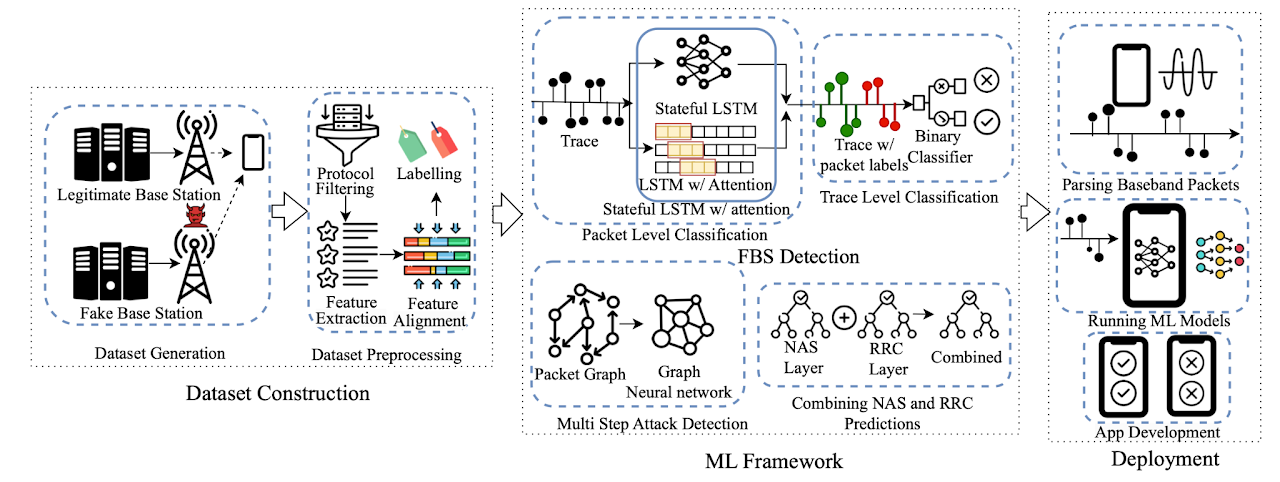
Fake base stations (FBSes) pose a significant security threat by impersonating legitimate base stations (BSes). Though efforts have been made to defeat this threat, up to this day, the presence of FBSes and the multi-step attacks (MSAs) stemming from them can lead to unauthorized surveillance, interception of sensitive information, and disruption of network services. Therefore, detecting these malicious entities is crucial to ensure the security and reliability of cellular networks. Traditional detection methods often rely on additional hardware, predefined rules, signal scanning, changes to protocol specifications, or cryptographic mechanisms that have limitations and incur huge infrastructure costs in accurately identifying FBSes. In this paper, we develop FBSDetector–an effective and efficient detection solution that can reliably detect FBSes and MSAs from layer-3 network traces using machine learning (ML) at the user equipment (UE) side. To develop FBSDetector, we create FBSAD and MSAD, the first-ever high-quality and large-scale datasets incorporating instances of FBSes and 21 MSAs. These datasets capture the network traces in different real-world cellular network scenarios (including mobility and different attacker capabilities) incorporating legitimate BSes and FBSes. Our novel ML framework, specifically designed to detect FBSes in a multi-level approach for packet classification using stateful LSTM with attention and trace level classification and MSAs using graph learning, can effectively detect FBSes with an accuracy of 96% and a false positive rate of 2.96%, and recognize MSAs with an accuracy of 86% and a false positive rate of 3.28%. We deploy FBSDetector as a real-world solution to protect end-users through a mobile app and validate it in real-world environments. Compared to the existing heuristic-based solutions that fail to detect FBSes, FBSDetector can detect FBSes in the wild in real time.
Imtiaz Karim*, Kazi Samin Mubasshir*m, and Elisa Bertino, (* joint first authors)
USENIX Security Symposium, 2025
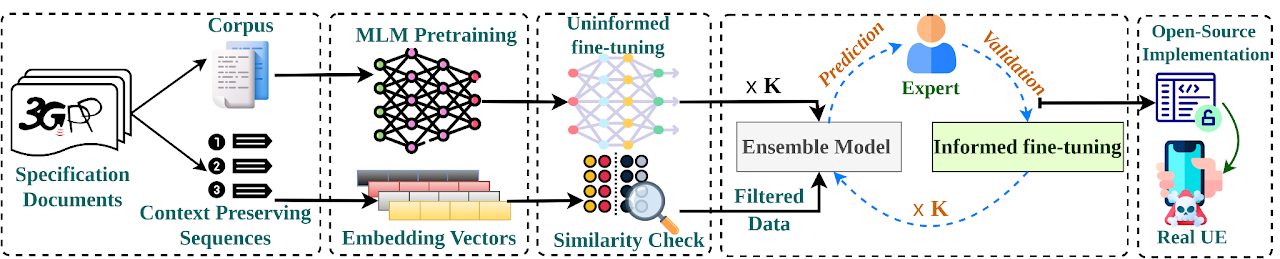
In recent years, there has been a growing focus on scrutinizing the security of cellular networks, often attributing security vulnerabilities to issues in the underlying protocol design descriptions. These protocol design specifications, typically extensive documents that are thousands of pages long, can harbor inaccuracies, underspecifications, implicit assumptions, and internal inconsistencies. In light of the evolving landscape, we introduce CellularLint–a semi-automatic framework for inconsistency detection within the standards of 4G and 5G, capitalizing on a suite of natural language processing techniques. Our proposed method uses a revamped few-shot learning mechanism on domain-adapted large language models. Pre-trained on a vast corpus of cellular network protocols, this method enables CellularLint to simultaneously detect inconsistencies at various levels of semantics and practical use cases. In doing so, CellularLint significantly advances the automated analysis of protocol specifications in a scalable fashion. In our investigation, we focused on the Non-Access-Stratum (NAS) and the security specifications of 4G and 5G networks, ultimately uncovering 157 inconsistencies with 82.67% accuracy. After verification of these inconsistencies on 3 open-source implementations and 17 commercial devices, we confirm that they indeed have a substantial impact on design decisions, potentially leading to concerns related to privacy, integrity, availability, and interoperability.
Imtiaz Karim*, Mirza Masfiqur Rahman*m, and Elisa Bertino, (* joint first authors)
USENIX Security Symposium, 2024
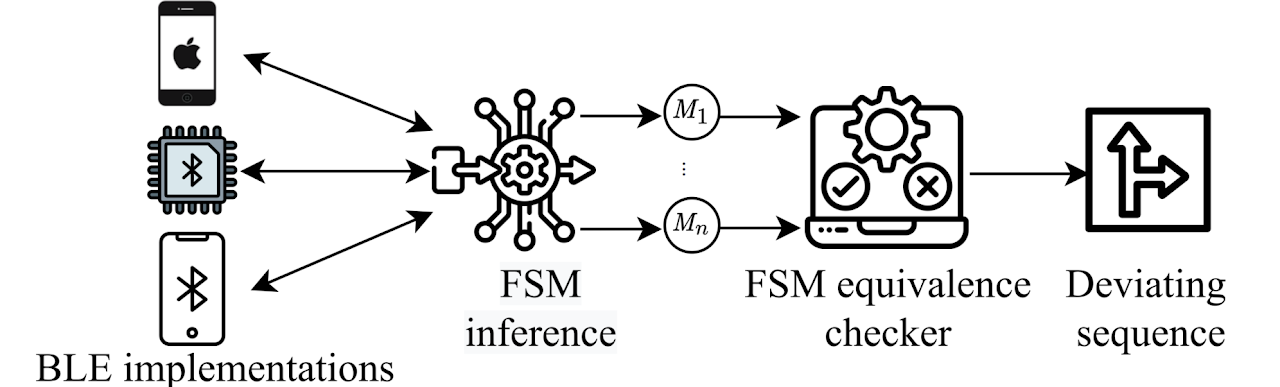
In this work, we develop an automated, scalable, property-agnostic, and black-box protocol noncompliance checking framework called BLEDiff that can analyze and uncover noncompliant behavior in the Bluetooth Low Energy (BLE) protocol implementations. To overcome the enormous manual effort of extracting BLE protocol reference behavioral abstraction and security properties from a large and complex BLE specification, BLEDiff takes advantage of having access to multiple BLE devices and leverages the concept of differential testing to automatically identify deviant noncompliant behavior. In this regard, BLEDiff first automatically extracts the protocol FSM of a BLE implementation using the active automata learning approach. To improve the scalability of active automata learning for the large and complex BLE protocol, BLEDiff explores the idea of using a divide and conquer approach. BLEDiff essentially divides the BLE protocol into multiple sub-protocols, identifies their dependencies and extracts the FSM of each sub-protocol separately, and finally composes them to create the large protocol FSM. These FSMs are then pair-wise tested to automatically identify diverse deviations. We evaluate BLEDiff with 25 different commercial devices and demonstrate it can uncover 13 different deviant behaviors with 10 exploitable attacks.
Imtiaz Karim, Abdullah Al Ishtiaq, Syed Rafiul Hussain, and Elisa Bertino
IEEE Symposium on Security and Privacy (IEEE S&P), 2023
(⚛)a and (⚛)m are students advised and mentored by me, respectively.
2026: Breaking 5G on The Lower Layer
Subangkar Karmaker Shantom, Imtiaz Karim, Elisa Bertino
Workshop on Security and Privacy of Next-Generation Networks (FutureG), 2026 (co-located with NDSS).
2026: VWAttakcer: A Systematic Security Testing Framework for Voice over WiFi User Equipments [PDF]
Imtiaz Karim*, Hyunwoo Lee*, Hassan Asghar, Kazi Samin Mubasshirm, Seulgi Han, Mashroor Hasan Bhuiyana, and Elisa Bertino, (* joint first authors)
IEEE International Conference on Computer Communications (INFOCOM), 2026
2025: Mission Explainable: From Feature Attribution to Mitigation in 5G Anomaly Detection
Federica Uccello, Imtiaz Karim, Kazi Samin Mubasshirm, Elisa Bertino, Simin Nadjm-Tehrani
International Conference on Computing, Networking and Communications (ICNC), 2025
2026: TIMESAFE: Timing Interruption Monitoring and Security Assessment for Fronthaul Environments
Joshua Groen, Simone Di Valerio, Imtiaz Karim, Davide Villa, Yiwei Zhangm, Leonardo Bonati, Michele Polese, Salvatore D’Oro, Tomasso Melodia, Elisa Bertino, Francesca Cuomo, and Kaushik Chowdhury
ACM Transaction on Privacy and Security (ACM TOPS), 2025.
2026: LLMalMorph: On The Feasibility of Generating Variant Malware using Large-Language-Models
Md Ajwad Akilm, Adrian Shuai Li, Imtiaz Karim, Arun Iyengar, Ashish Kundu, Vinny Parla, Elisa Bertino
IEEE International Conference on Trust, Privacy and Security in Intelligent Systems and Applications (IEEE TPS), 2025.
2026: WCDCAnalyzer: Scalable Security Analysis of Wi-Fi Certified Device Connectivity Protocols [PDF]
Zilin Shenm, Imtiaz Karim, and Elisa Bertino
Network and Distributed System Security Symposium (NDSS), 2026.
2025: Security Opportunities and Challenges for Disaggregated Architectures
Elisa Bertino, Imtiaz Karim, and Ashish Kundu
Design Automation Conference (DAC), 2025 (invited paper).
2025: Standing Firm in 5G: A Single-Round, Dropout-Resilient Secure Aggregation for Federated Learning
Yiwei Zhangm, Rouzbeh Behnia, Imtiaz Karim, Attila A Yavuz and Elisa Bertino
ACM Conference on Security and Privacy in Wireless and Mobile Networks (WiSec), 2025.
2025: How Feasible is Augmenting Fake Nodes with Learnable Features as a counter-strategy against Link Stealing Attacks? [PDF]
Mir Imtiaz Mostafizm, Imtiaz Karim and Elisa Bertino
ACM Conference on Data and Application Security and Privacy (CODASPY), 2025.
2025: AKMA+: Privacy-Enhanced and Standard-Compatible AKMA for 5G Communications [PDF]
Yang Yang, Guomin Yang, Yingjiu Li, Minming Huang, Zilin Shenm, Imtiaz Karim, Ralf Sasse, David Basin, Elisa Bertino, Jian Weng, Hwee Hwa Pang, and Robert H. Deng
USENIX Security Symposium, 2025.
2024: Gotta Detect ’Em All: Fake Base Station and Multi-Step Attack Detection in Cellular Networks [PDF]
Imtiaz Karim*, Kazi Samin Mubasshir*m, and Elisa Bertino, (* joint first authors)
USENIX Security Symposium, 2025
2024: CellularLint: A Systematic Approach to Identify Inconsistent Behavior in Cellular Network Specifications [PDF]
Imtiaz Karim*, Mirza Masfiqur Rahman*m, and Elisa Bertino, (* joint first authors)
USENIX Security Symposium, 2024
2024: Security Attacks to the Name Management Protocol in Vehicular Networks [PDF]
Sharika Kumarm, Imtiaz Karim, Elisa Bertino, and Anish Arora
Symposium on Vehicle Security and Privacy (VehicleSec), 2024.
2024: Segment-Based Formal Verification of WiFi Fragmentation and Power Save Mode [PDF]
Zilin Shenm, Imtiaz Karim, and Elisa Bertino
ACM ASIA Conference on Computer and Communications Security (ASIACCS), 2024.
2023: SPEC5G: A Dataset for 5G Cellular Network Protocol Analysis [PDF]
Imtiaz Karim, Kazi Samin Mubasshirm, Mirza Masfiqur Rahmanm, and Elisa Bertino
International Joint Conference on Natural Language Processing and the Conference of the Asia-Pacific Chapter of the Association for Computational Linguistics (IJCNLP-AACL), 2023.
2023: BLEDiff: Scalable and Property-Agnostic Noncompliance Checking for BLE Implementations [PDF]
Imtiaz Karim, Abdullah Al Ishtiaq, Syed Rafiul Hussain, and Elisa Bertino
IEEE Symposium on Security and Privacy (IEEE S&P), 2023
2022: VWAnalyzer: A Systematic Security Analysis Framework for the Voice over WiFi Protocol [PDF]
Hyunwoo Lee, Imtiaz Karim, Ninghui Li, and Elisa Bertino
ACM ASIA Conference on Computer and Communications Security (ASIACCS), 2022.
2021: AI-powered Network Security: Approaches and Research Directions [PDF]
Elisa Bertino and Imtiaz Karim
International Conference on Networking, Systems, and Security (NSysS), 2021 (Research directional paper).
2021: Noncompliance as Deviant Behavior: An Automated Black-box Noncompliance Checker for 4G LTE Cellular Devices [PDF]
Imtiaz Karim*, Syed Rafiul Hussain *, Abdullah Al Ishtiaq, Omar Chowdhury, and Elisa Bertino (* joint first authors)
ACM Conference on Computer (CCS), 2021
2021: ProChecker: An Automated Security and Privacy Analysis Framework for 4G LTE Protocol Implementations [PDF]
Elisa Bertino and Imtiaz Karim
International Conference on Networking, Systems, and Security (NSysS), 2021 (Research directional paper).
2020: ATFuzzer: Dynamic Analysis Framework of AT Interface for Android Smartphones [PDF]
Imtiaz Karim, Fabrizio Cicala, Syed Rafiul Hussain, Omar Chowdhury, and Elisa Bertino </u>
ACM Digital Threats Research and Practice (DTRAP), 2020.
2019: Opening Pandora’s Box through ATFuzzer: Dynamic Analysis of AT Interface for Android Smartphones
[PDF]
Imtiaz Karim, Fabrizio Cicala, Syed Rafiul Hussain, Omar Chowdhury, and Elisa Bertino </u>
Annual Computer Security Applications Conference (ACSAC), 2019.
2019: 5GReasoner: A Property-Directed Security and Privacy Analysis Framework for 5G Cellular Network Protocol [PDF]
Syed Rafiul Hussain, Mitziu Echeverria, Imtiaz Karim, Omar Chowdhury, and Elisa Bertino
ACM Conference on Computer and Communications Security (CCS), 2019.
2018: Maximizing Heterogeneous Coverage in Over and Under Provisioned Visual Sensor Networks [PDF]
Abdullah Al Zishan, Imtiaz Karim, Sudipta Saha Shubha, Ashikur Rahman
The Journal of Network and Computer Applications, Elsevier (JNCA), Volume 124, 15 December 2018, Pages 44-62.
2023: Machine Learning Techniques for Cybersecurity
Elisa Bertino , Sonam Bhardwaj , Fabrizio Cicala , Sishuai Gong , Imtiaz Karim , Charalampos Katsis , Hyunwoo Lee , Adrian Shuai Li , Ashraf Y. Mahgoub
Synthesis Lectures on Information Security, Privacy, and Trust (SLISPT), Springer Nature, May 2023.
2023: A Systematic Framework for Analyzing The Security And Privacy of Wireless Communication
Imtiaz Karim
Ph.D. Thesis, Purdue University, 2023
2020: ProChecker: An Automated Security and Privacy Analysis Framework for Communication Protocol Implementations
Imtiaz Karim, Sayak Ray, Arun Kanuparthi, and Jason M. Fung
Intel Software Practitioners Conference (Intel SWPC) 2020.
2020: Utilizing Symbolic Execution for Property-Guided Security and Privacy Testing in Communication Protocol Implementations
Imtiaz Karim, Sayak Ray, Arun Kanuparthi, Stephan Heuser and Jason M. Fung
Intel Software Practitioners Conference (Intel SWPC) 2020.